With the increasing rate of cyberattacks, many IT executives and Data Center operators spend a significant amount of time and money trying to mitigate risks and stay secure. While cybersecurity is crucial, it is equally expedient not to ignore the dangers posed by your data centers, either on-prem or colocated. Physical security plays a significant role in ensuring the safety of the infrastructure that enable the digital presence of your business.
In this blog, we’ll share six best practices that can help you mitigate the risks facing your physical data centers (On-prem infrastructure or Colocated):
Best Practice 1 – Establish a multi-layered security perimeter
The server, storage and networking equipment in your data centers are extremely valuable to your business, but only if it remains online. This means you need multiple layers of protection between your equipment and all those who may wish your business harm. It’s a very simple concept, but it can be deceptively hard to execute.
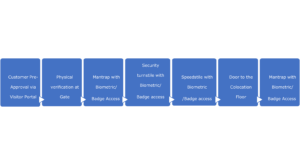
At all MDXi Data Centers, visitors are required to pass through seven (7) layers of physical security before they’d be able to access customer equipment:
These layers provide multiple opportunities to identify unauthorized visitors and deny them access. The mantrap is used to control ingress and egress from the facility, and thus prevent “tailgating”—when an unauthorized visitor attempts to access the facility by following a legitimate visitor in.
Best Practice 2 – Institute robust physical and logical access controls
An effective approach to data center security is ensuring a balance between keeping equipment protected and not making things too difficult for those who do have a legitimate reason to access the facility.
For this reason, you must integrate your physical security strategy with your logical security strategy. Anyone with a valid reason to visit the data center should be able to request authorized access in advance using a clearly defined process. to shorten the security process and avoid unnecessary delays.
Regular authorized visitors who visit the facility frequently can utilize secure and encrypted access readers based on their stored biometric profile, allowing them to quickly pass access controls during any subsequent visits.
Best Practice 3 – Conduct continuous monitoring
Physical data center security can also take a pointer from cybersecurity through the concept of zero-trust security. Zero trust does away with the idea of only trusting network perimeters. Instead, all entities are subject to recurring authentication challenges and constant monitoring, regardless of whether they’re inside the perimeter or outside.
In a similar way, your physical security efforts shouldn’t end once a visitor is through the door. Just because someone is trusted to enter doesn’t mean they can be trusted to do whatever they want inside the facility. All MDXi Data Center facilities use CCTV cameras, motion sensors and additional biometric scanners placed at different points throughout the facility, thus ensuring visitors only access the specific customer equipment they are authorized to access.
Environmental monitoring techniques help protect our data centers against threats both from malicious actors and from other sources, such as fires. This is extremely important at a time when several recent data center fires have caused significant disruption for the affected companies.
Best Practice 4 – Perform regular testing to better understand risks in context
Conducting testing and drills at regular intervals can help you better understand the vulnerabilities in your data center, and how to address them. This would include tabletop exercises (TTXs) and penetration testing, which simulates an attacker trying to sneak their way into the facility. These tests help show that having the right monitoring and access control technology is only one part of a comprehensive physical security strategy. There’s also a human angle to account for.
Penetration testers help identify areas where guards or other employees may be the weak link in the security chain. For instance, if an employee were to leave a fire door propped open while they step outside to take a break, it could undermine the security perimeter mentioned earlier. In addition, threat monitoring can help you understand the risks facing your data centers in advance.
Best Practice 5 – Empower people to be a part of the solution
You can account for the human angle by empowering employees to play their part in the overall security strategy. To do this, it’s important to give them the right training and industry certification opportunities.
Certifications help ensure employees understand and can apply industry-accepted best practices for physical data center security. They can also be helpful to demonstrate compliance with applicable data privacy regulations in your local jurisdictions, and to provide assurance to customers whose sensitive data are hosted in the data center
MDXi Data Center facilities in Nigeria, Ghana and Cote d’Ivoire are built and operated in accordance with numerous industry standards and certification programs, including the Tier III Constructed Facility certification (TCCF); the PCI-DSS certification which certifies the Data center to process payment card information; ISO 27001 and ISO 9001 certifications which assures information security and quality management.
Best Practice 6 – Design data centers for built-in resiliency
It’s not always possible to ward off every risk facing your data center therefore it’s important to design data centers with built-in redundancy. This would include power, geographic and network redundancy.
All MDXi regional data centers offer fully redundant primary power feeds, backup generators, and uninterruptable power supply (UPS) systems—both for the data center and critical mechanical equipment. Our customers can connect their equipment to these redundant power systems via dual power circuit feeds, allowing for seamless failover in the event one of the circuits goes down.
Next steps?
Mitigating risks in physical data centers is a multi-faceted undertaking that requires the right combination of strategy, architecture, technology, and processes. To read more on data center risk mitigation and best practices, click here
Want to mitigate your Data Center against risk and cyber security? Talk to an expert here